CYBERSECURITY POSTURE
Last updated September 2022
SAIM employs a multi-pronged approach to cybersecurity that includes: user management, application security and monitoring, data transfer protocols and written policies for audits and reviews conducted annually and, in some cases, more frequently.
9.1 APPLICATION SECURITY
9.1.1 NIST 800-171
SAIM is committed to meeting the application security standards of NIST 800-171. SAIM has worked with RSM US LLP (RSM) to perform a gap assessment against security requirements as defined in the National Institute of Standards and Technology (NIST) Special Publication (DP) 800-171. These requirements are a component of the Department of Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012.
NIST 800-171 was developed after the Federal Information Security Management Act (FISMA) was passed in 2003, resulting in several security standards and guidelines. NIST 800-171 was created to improve cybersecurity, especially after numerous, well-documented breaches in the last few years, including the United States Postal Service (USPS) and National Oceanic and Atmospheric Administration (NOAA). The NIST says it is “a national imperative” to ensure unclassified information that isn’t part of federal information systems and organizations is properly protected and consistent to help the federal government “successfully carry out its designated missions and business operations.”
At the time of the assessment (June 2021), SAIM had 90% of all NIST SP 800-171 requirements completely in place and 95% partially or fully in place. This assessment covered awareness training, audit and accountability, configuration management, identification and authentication, personnel security, physical protection, communications protection, and system/information protection. Since the initial audit, SAIM has completed the remaining requirements and will engage RSM US LLP for a follow-up audit in the calendar year 2023. A copy of the initial audit is available upon request.
SAIM consistently maintains security operations, as demonstrated in its Security Policy. The NIST SP 800-171 minimum security requirements include necessary controls in about 110 specific areas, across 14 families, including:
- Access Control
- Awareness and Training
- Audit and Accountability
- Configuration Management
- Identification and Authentication
- IR
- Maintenance
- Media Protection
- Personnel Security
- Physical Protection
- Risk Assessment
- Security Assessment
- System and Communications Protection
- System and Information Integrity
9.1.2 GENERAL APPLICATION SECURITY FACTS
- The SAIM application is hosted on Microsoft Azure, and access is only possible via a B2C gateway through Azure.
- Any third-party applications in support of SAIM are vetted and required to meet the minimum requirements of SAIM or better. Currently, all third-party applications are SOC certified and, in many cases, with multiple additional security certifications.
- SAIM uses Open ID Connect (OIDC) to securely authenticate users to our native application services and any third-party applications that support the SAIM modules. OIDC is the industry standard for securely authenticating users across websites, apps, and web services without sharing passwords.
- SAIM collects the following data examples:
- User Information
- FNAME
- LNAME
- Business Email
- Documentation
- Facility Records
- Specifications
- Datasheets
- Equipment Documents
- Assets Paperwork
- Misc. Facility and Audit Documentation
- Asset Maintenance Records
- Maintenance Logs
- Georeferencing Information
- Execution Time Logs
- Cost Analysis
- Manhours
- Codes and Standards Names
- Workorders
- Execution Attachments (pictures, signup sheets, test records, etc.)
- Visualization
- Facility Pictures
- 3D CAD Models
- Survey Coordinates
- Dimensional Requirements
- Real-Time Monitoring Signals
- All Instrumentation Signals
- Temperature
- Fuel Level
- Volumes
- Pressure
- Vibration
- Etc.
- User Information
- The information, infrastructure, datacenters, and users are currently only within North America (the United States and later Canada).
- SAIM currently does not share or sell the data with any affiliates or 3rd parties.
- Users are granted access only upon approval by the Owner/Client, based on their assigned role.
- Security of the data in SAIM's possession (in transit/at rest) is as follows:
- Data in transit across public networks is protected by industry-standard encryption protocols. These protocols provide data privacy, prevent in-transit data observation, and ensure data integrity by preventing the data from being altered in transit.
- Data stored within SAIM is protected by layered access control. Systems and people are individually authenticated to ensure "least privilege" data access.
- Facility IoT (Internet of Things) data are subject to standard security measures determined in partnership with the facility.
- Security of the data NOT in SAIM's possession (in transit/at rest) is as follows:
- Direct communication between SAIM and third-party modules, such as single sign-on information via OpenID Connect, is always secured.
9.1.3 SAIM SECURITY POLICIES
SAIM Security Policies include comprehensive documentation of the following policies with associated procedures and actions required to support and comply with the applicable policies. Included in that document are the following policy/plan titles:
- SAIM Incident Response Plan
- SAIM Risk Management Plan
- Third Party Information Security Risk Management Policy
- Vulnerability Assessment Policy
- Bring Your Own Device Policy
- Business Continuity/Disaster Recovery Plan
SAIM follows our Security Policies document, which provides the impetus for security and business teams to integrate their efforts from the perspective of awareness and communication, as well as coordinated response in times of crisis (security vulnerability identified or exploited). A copy of the SAIM Security Policy Document is available upon request. Specifically, the Security Policies include contact information, escalation paths, expected service level agreements (SLA), severity and impact classification and mitigation/remediation timelines. Incorporating these policies as new products or services are developed and prepared for release ensures that any opportunity for a security incident is mitigated and that swift mitigation and remediation ensues in the rare instance of an incident.
The current SAIM Incident Management Plan is fully integrated with our cybersecurity posture. It has been developed to provide direction and focus to handling information security incidents that adversely affect SAIM Information Resources. The SAIM Incident Management Plan aims to allow SAIM to respond quickly and appropriately to SAIM information security incidents.
9.2 REAL-TIME SIGNALS MONITORING DATA SECURITY
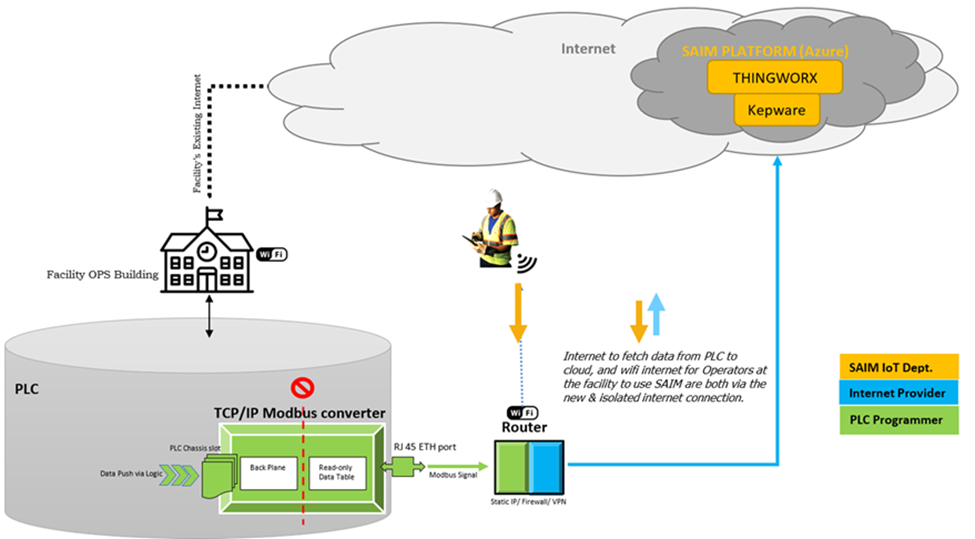
SAIM collaborated with Menzies' cybersecurity department to establish a workflow that conforms to the latest TSA requirements optimized and released after the Colonial Pipeline incident. The team defined a state-of-the-art connection architecture that honors all the project goals.
This security workflow includes the following enhanced security protocols:
- Isolated network from facility's PLC/Controls
- Read-only Data Transmission
- End-to-End Data Encryption
- IT controls such as firewall, VPN, and industry-grade security hardware
The topology of this architecture looks like this:
9.3 CYBERSECURITY RECAP
- SAIM's portfolio does not interfere with facility operations and is not capable of controlling any systems at the facility.
- SAIM cannot push any data back to the facility's control systems or instrumentation.
- SAIM cannot cause any disruption or threat to the facility's operations.
- SAIM does not collect or store any sensitive personal information. The information collected from the users is limited to First Name, Last Name, Email and Facility Address.
- SAIM performs bi-annual cybersecurity audits, including penetration tests and risk assessments through third-party cybersecurity subject matter experts.
- SAIM IT team continuously checks the system-level monitoring, network security and firewalls.
- The primary data center hosting SAIM's portfolio is Microsoft Azure benefiting from industry-standard security practices. Access to the SAIM platform is only possible via a single B2C gateway.
- SAIM's third-party modules are supplied by reputable vendors that follow industry-standard security procedures.
- SAIM continuously collaborates with its third-party suppliers to enforce security best practices.
- SAIM's authentication process is based on multi-factor single sign-on, and the main third-party modules are connected via Open ID Connect (OIDC) authentication protocols. Direct communication between SAIM and third-party modules, such as single sign-on information via OpenID connect, is always secured.
- Data in transit across public networks is protected by industry-standard encryption protocols. These protocols provide data privacy, prevent in-transit data observation, and ensure data integrity by preventing the data from being altered in transit.
- Data stored within SAIM is protected by layered access control. Systems and people are individually authenticated to ensure "least privilege" data access.
- SAIM's Backup Strategy includes the storage of SAIM and IoT backups. These backups are "locally redundant," which provides recovery from data loss within our deployed region/data center, Central US.
